A recently published and widely quoted report by Chainalysis on ransomware revenues (https://www.chainalysis.com/blog/ransomware-2024/) clearly indicated the volume of extorted cryptocurrency payments from victims had soared in 2023. The numbers broke the $1Bn to the record high $1.1Bn and beyond. For some this came as a surprise after we all witnessed the decline in both number of attacks and revenues witnessed in 2022.
Ransomware revenue trends
In 2023, ransomware threat actors intensified their operations, targeting high-profile institutions, critical infrastructure, and corporations as well as much smaller businesses. Some of the taboos of previous years were also broken, for instance attacks on the healthcare sector, which was previously omitted by some of the larger ransomware syndicates. Major ransomware supply chain attacks were carried out exploiting the ubiquitous file transfer software MOVEit, impacting organizations and companies worldwide.
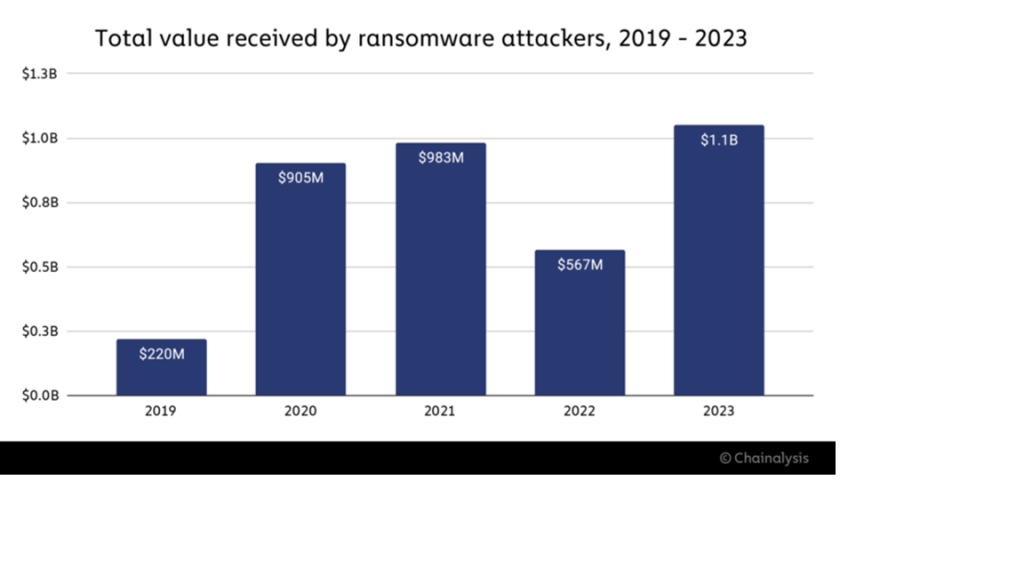
Ransomware payments in 2023 surpassed the $1 billion mark, the highest number ever observed. Although 2022 saw a decline in ransomware payment volume, the overall trend line from 2019 to 2023 indicates that ransomware is an escalating problem. We should also keep in mind that the volume of ransomware payments does not capture the whole economic impact of productivity loss, incident response and repair costs, as well as legal costs and reputational damage associated with the attacks.
The reported decline in ransomware in 2022 could likely be due to geopolitical events such as the Russian-Ukrainian war. This conflict has likely disrupted the operations of some cyber actors but also shifted their focus from financial gain to politically motivated cyberattacks aimed at espionage and cyber warfare by nation states. Another significant factor in the reduction of ransomware in 2022 was the successful infiltration of the Hive ransomware syndicate, ranked in 2022 as the fifth most active by Malwarebytes (https://www.malwarebytes.com/blog/news/2023/01/hive-ransomware-infrastructure-taken-down) .
The evolving threat landscape
The year 2023 marks a major comeback for ransomware, not only with the record-breaking volume of payments but also with the number, scope, complexity, and sophistication of the attacks as well as the number of new threat actors emerged this year.
The continually evolving threat landscape of ransomware is expanding, making it challenging to monitor every incident or trace all ransom payments made in cryptocurrencies. It is important to recognize that the figures published by Chainalysis, and others tend to be conservative estimates, likely to increase as new ransomware addresses are discovered over time. For instance, the initial reporting by Chainalysis for 2022 showed $457 million in ransoms, but this figure has since been revised upward by 24.1%.
The number of ransomware threat actors had also significantly grown in 2023 comprised of a variety of players, from individuals and small criminal groups to departmentalized crime syndicates such as LockBit or BlackCat/AlphV reigning at the top. The total size of the ransomware industry is currently estimated by several hundreds of threat actors.
Different ransomware threat actors employ different strategies. Some are on the prowl for large corporations seeking big-number revenue. Usually this comes at the price of running fewer attacks. Others launch carpet-bombing attacks at small and medium businesses counting on their lower level of preparedness to face a cyber crisis and susceptibility to payment. The larger Ransomware as a Service (RaaS) crime syndicates attack across the board. From multi-national corporations and government agencies to small family businesses. These mega-groups outsource to subcontractors, colloquially known as affiliates. The affiliates are granted access to the malware to carry out attacks, and in exchange pay the syndicate core operators a cut of the ransom received.
The trend of RaaS has also effectively lowered the technological proficiency threshold, compared to previous years when threat actors had to be highly skilled hackers to launch successful ransomware attacks. Today the proliferation of RaaS allows almost anyone to use prefabricated strain-kits to launch attacks on the less prepared and collect the criminal payouts.
Here is what we’ve learned from the trends of ransomware in 2023:
- The ransomware landscape underwent significant changes in 2023, marked by shifts in tactics and affiliations among threat actors, as well as the continued spread of RaaS strains and swifter attack execution, demonstrating a more efficient and aggressive approach.
- Threat actors keep reinventing themselves, seeking more lucrative, efficient, and robust extortion strategies and methods of operation to flourish.
- Unfortunately, ransomware is too large and profitable an industry to just disappear into the sunset. As long as nation states allow ransomware operators to devise attacks with relative impunity the trend of ransomware growth is expected to continue. Effectively combating ransomware requires a type of cross-global cooperation we are yet to see.
Conclusion
Looking back to our blog post of January 21st, 2023 at https://cipteam.com/ransomware-2022-2023-profits-drop-and-threat-landscape-granulating-are-these-connected/ one can clearly see that most of the assessment discussed for 2023 was proven right. Not only ransomware did not disappear, but it also remained a major threat. Moreover, it increased in magnitude and revenue. The number and variety of threat actors grew significantly.
So, what about 2024? Similar to our projection for 2023, assessment is that ransomware isn’t going anywhere. It will become even more sophisticated than in 2023 as generative AI is increasingly being weaponized to create smarter, stealthier code that is better able to evade detection and streamline attacks. A significant move by threat actors will be to move away from data encryption to data exfiltration and victim extortion to refrain from publishing it. To match the proliferation of ransomware the regulatory requirements are also expected to grow, putting additional preparedness and reporting burdens on businesses and organizations.
Looking at the threat landscape we expect additional growth and granulation of the cyber-criminal-underworld with the technological threshold staying low, allowing additional players to join the party, including traditional criminal organizations, picking money on the ground.
These were the sad news. The better ones are that businesses shouldn’t think they are doomed and that there is nothing one can do to improve its cyber posture and resilience.
It would be correct to state that organizations have close to no control over the question of whether they will be attacked or not. Today’s reality is that ransomware is an issue of ‘When’ rather than the one of ‘If’ . But what happens after the threat actor zeroes his sights on your organization is a different ball game. Businesses and organizations that took the threat seriously investing in ransomware preparedness, namely, the use of threat intelligence tools, awareness by employees and senior management alike, perimeter defense, up-to-date emergency protocols are more likely to be for-warned and avoid the incident altogether or at the least mitigate its financial, reputational, and other consequences. CIPTeam prides itself on assisting organizations to be prepared, and if bad comes to worse offers expert assistance and support in overcoming the crisis. We’ve been there, successfully managing ransomware and other cyber related crises worldwide. Contact us at info@cipteam.com to bolster your cyber resilience.
